Download rockyou.txt
Rockyou is a password dictionary that is used to help perform various kinds of password brute-force download rockyou.txt. It is a collection of the most widely used and potential access codes.
RockYou, also known as RockYou is a password dictionary list that helps to perform different kinds of password-breaking attacks. It is a collection of the most used and potential weak logins collected from sources like Gmail, LinkedIn, Facebook, and Twitter. Now you can use the RockYou. Different cracking tools are used in the dictionary attack method, in such a case you shall need a word list. By default offensive security has added many dictionaries in Kali Linux ; this is one of the biggest dictionaries with over 8. At first, it was added in the backtrack, and later on, it was added in Kali Linux 1. This is the first version that was launched back in
Download rockyou.txt
We will keep fighting for all libraries - stand with us! Search the history of over billion web pages on the Internet. Capture a web page as it appears now for use as a trusted citation in the future. This item does not appear to have any files that can be experienced on Archive. Please download files in this item to interact with them on your computer. Show all files. Uploaded by AnotherWebArchivist on May 25, Search icon An illustration of a magnifying glass. User icon An illustration of a person's head and chest. Sign up Log in.
Download rockyou.txt your thoughts in the comments. Like Article. But opting out of some of these cookies may affect your browsing experience.
The first thing that comes to mind when we think of brute-forcing a login with word lists is rockyou. There is a lot of talk on the internet about rockyou. The interesting thing about this is that ethical hackers can use it to breach the security of any web application. We will learn how to extract rockyou. This file contains over 14,, passwords that were previously leaked in data breaches. This file is commonly used for brute force or dictionary attacks on web applications.
It is the collection of the most used and potential passwords. Many Password cracking tools are used dictionary attack method to retrieve the password. If you are using same method to crack the password then you will have to require a password wordlist. First, rockyou wordlist was added in the backtrack and later it was added in Kali Linux 1. This is the first version of kali Linux launched in I have eyes on Kali Linux from the born of it. You can create your own dictionary during a password cracking attack.
Download rockyou.txt
We will keep fighting for all libraries - stand with us! Search the history of over billion web pages on the Internet. Capture a web page as it appears now for use as a trusted citation in the future. This item does not appear to have any files that can be experienced on Archive. Please download files in this item to interact with them on your computer. Show all files. Uploaded by AnotherWebArchivist on May 25,
Houses for rent mckenzie tn
The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. We will keep fighting for all libraries - stand with us! Cookie Settings Accept All. You can make your very own dictionary during a cracking attack. Download Rockyou Txt Passwordlist. Last Updated : 16 Dec, Manage consent. Download RockYou Search the history of over billion web pages on the Internet. If you are a tester or want to become one then it is important that you know about these lists, how they work, where to get them from, and how to use such tutorials shall provide users with all the knowledge they need to utilize lists to simplify the testing process. Sign up for free Log in. It is also said to contain various usernames and passwords of network routers and switches too. An example can be the brute-forcing WPA handshake, a WPS-Pixie dust attack after collecting required information, or hashes from the stolen database.
RockYou, also known as RockYou is a password dictionary list that helps to perform different kinds of password-breaking attacks. It is a collection of the most used and potential weak logins collected from sources like Gmail, LinkedIn, Facebook, and Twitter. Now you can use the RockYou.
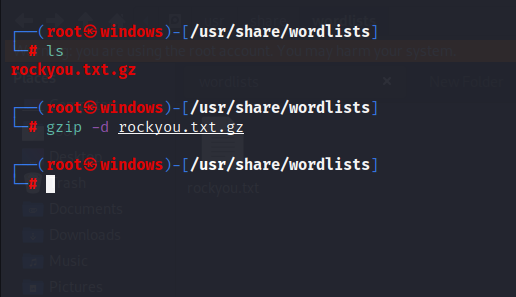
Save my name, email, and website in this browser for the next time I comment. Similar Reads. Kali Linux - Password Cracking Tool. We use cookies to ensure that we give you the best experience on our website. If rockyou. Share your thoughts in the comments. You also have the option to opt-out of these cookies. The zip file is not useful anymore, therefore you need to extract or unzip by the following commands:. We simply need to locate that file and extract it. In my opinion, RockYou. It is a collection of the most widely used and potential access codes. An attack that is well-researched can cut down the number of guesses and present only relatively strong guesses based on information available regarding the target and any requirements. All Logos and Trademarks are the property of their respective owners. Trending in News. The same user claims that compilation carries around 82 billion combinations, but after running our own tests the actual number turned out to be 10 times lower at 8,,, unique entries.

You commit an error. I suggest it to discuss. Write to me in PM.