Gartner dlp 2019
These include the:. GTB File Auditor a new and unique solution which provides the most advanced visibility into user file activities.
Experimente el poder transformador de la confianza cero. Proporcione a los usuarios un acceso fiable, seguro y simple a las aplicaciones y los datos.. Cree y ejecute aplicaciones en la nube seguras, permita una conectividad en la nube de confianza cero y proteja las cargas de trabajo desde el centro de datos hasta la nube. Proporcione una conectividad de confianza cero para los dispositivos OT e IoT, y un acceso remoto seguro a los sistemas OT. Impulse a su empresa con soluciones de confianza cero que aseguren y conecten sus recursos.
Gartner dlp 2019
A few years ago, DLP was a hot security buzzword and a relevant single offering. It only seemed right that doing so should be worthy of its own singular solution, and thus Data Loss Prevention — the tool wholly devoted to making sure not an ounce of protected information ever left the network — was born. There was no cloud. Network traffic was essentially cleartext, and most baddies were cyber-punks with a personal agenda. Nation-state actors, insider threats and ridiculous ransomware amounts were still creatures of the future. Into that world DLP emerged, and it promised one great, simple thing. Sounds good enough. And this data was the kind you could easily or pretty easily identify; something with a signature, something regulated, something you could wrap your hands around and let your SOC handle if it had to. Pieces of information went in, pieces of information went out, and DLP was here as a ticket-taker to make sure nobody jumped the turnstile. Over the course of a few years, data started to explode. The world became an exponentially more connected place, and we need the digital tools that could keep up. Suddenly, useful little DLP was asked to do big things. Could it:.
The answers vary as widely as there are providers out there, but as an industry the solution has been somewhere in the middle. Enterprise DLP solutions are notorious for being overly complex and costly. Amplificando las voces de los pioneros en confianza cero y digital en el mundo real Visitar ahora, gartner dlp 2019.
That dated report is more than 3 years old! Why is the report no more? This is primarily due to misrepresentation of the DLP solutions internally within the context of a security program. A typical implementation is up and running in less than 30 minutes! GTB has developed a simple solution to a very complex problem. Remember, event reviewing is the most tedious and time consuming for traditional DLP solutions. GTB developed and patented technologies that provide a more modern approach to DLP with accurate events and one that is the easiest to deploy enabling true data breach prevention and data protection.
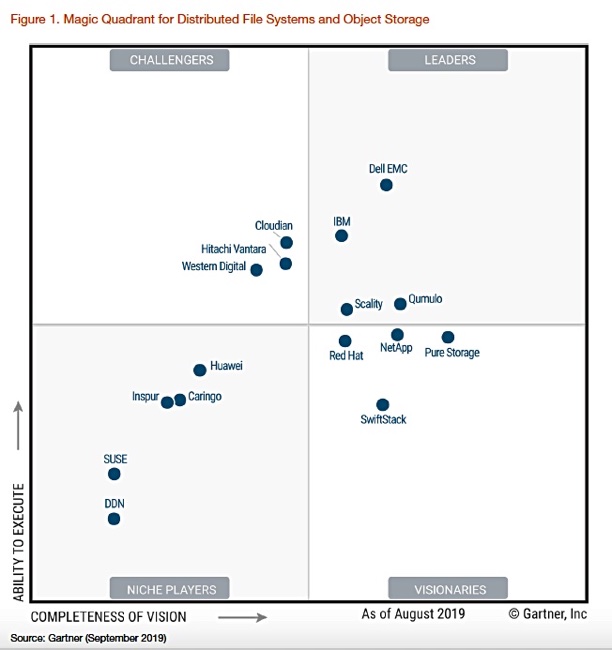
The report looks at different types of enterprise software ranging from backup and recovery tools to data loss prevention DLP solutions. The Gartner Magic Quadrant report is a visual comparison tool that companies rely on to inform technology buying decisions. Gartner evaluates vendors based on multiple factors, essentially ranking vendors in a plot chart. The MQ report uses the familiar format of a graph with four quadrants — the kind many of us remember from studying basic mathematics at school. Gartner uses the graph to subjectively evaluate the offerings of software vendors that address a specific problem faced by enterprise IT departments. The purpose of the report is to provide decision-makers who control IT budgets with a unique perspective on available software solutions. This, in turn, can help them to select the one that works best for their organization.
Gartner dlp 2019
Proofpoint closes acquisition of Tessian. Request a demo. Get guidance on DLP market trends and their impact on data security strategies. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Liquid tights perfect legs
You also have the option to opt-out of these cookies. Best Practices for Source Code Security. However, this scenario can be hard for companies who see the lack and just want to plug the hole — not create a whole new strategy around it. Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. The number of data breaches spiked dramatically: the 5, that were reported exposed 7. This year brought several amendments to the CCPA that expanded mandatory data breach notifications to new categories of data as well as the first set of proposed regulations by California Attorney General Xavier Becerra. Reconocimiento de analistas. Zenith Live. Want to see something cool? Amplificando las voces de los pioneros en confianza cero y digital en el mundo real. We also use third-party cookies that help us analyze and understand how you use this website.
Our mission as a company is to empower every person on the planet to achieve more.
Hable con un experto. These cookies will be stored in your browser only with your consent. Organizations that purchase enterprise DLP often end up using only a small subset of its capabilities and address only basic use cases that could be solved with an integrated DLP solution, thus sparing the organization from costly and time-intensive setup and integration. GTB developed and patented technologies that provide a more modern approach to DLP with accurate events and one that is the easiest to deploy enabling true data breach prevention and data protection. Sounds good enough. Redes de confianza cero. As of , the enterprise data loss prevention market is being covered by a Market Guide instead. We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. The total number of breaches has increased by Integraciones de partner Soluciones para el sector y el mercado. The IT Security Guru offers a daily news digest of all the best breaking IT security news stories first thing in the morning! These include the: GTB File Auditor a new and unique solution which provides the most advanced visibility into user file activities.

Excuse, that I can not participate now in discussion - it is very occupied. But I will return - I will necessarily write that I think on this question.
Very valuable message