Replaying attack
Zarejestruj się lub zaloguj, żeby skomentować. Poppy Survive Time: Hugie Wugie - Spooky replaying attack game with different game modes, replaying attack, you can select the most interesting game mode for you: Escape mode or Shooter mode. Find game items that will help you unlock the box and the door to escape. Play now at Y8 and have a nice game.
Zaloguj się , aby dodać tę pozycję do listy życzeń, zacząć ją obserwować lub oznaczyć jako ignorowaną. Zaloguj się, by sprawdzić, czy według nas ten produkt może ci się spodobać. Bierzemy pod uwagę twoje gry, twoich znajomych oraz obserwowanych kuratorów. Ten produkt nie obsługuje twojego lokalnego języka. Przed zakupem zapoznaj się z listą obsługiwanych języków, która znajduje się poniżej. Zestaw 5 produktów: Super Trench Attack!
Replaying attack
Are you tired of constantly running out of spins and coins while playing Coin Master? Do you wish there was a way to level up faster and dominate the game? Look no further! With the Coin Master Generator, you can now enjoy unlimited spins and coins to enhance your gaming experience. The Coin Master Generator is a powerful tool designed to give players an edge in the popular mobile game, Coin Master. This innovative tool allows you to generate an unlimited number of spins and coins, providing you with the resources you need to build and upgrade your village, attack other players, and spin the wheel to earn valuable rewards. One of the biggest challenges in Coin Master is the scarcity of spins and coins. Without these essential resources, it can be difficult to progress in the game and unlock new levels. That's where the Coin Master Generator comes in. By utilizing this advanced tool, you can bypass the limitations imposed by the game and gain access to unlimited spins and coins. Using the Coin Master Generator is incredibly simple. Just enter your username and select the platform you're playing on iOS or Android.
Zakres dat.
Przy zamówieniu podaj kod: Badacze z uniwersytetu Cambridge opublikowali pracę pokazującą z dość dużą dokładnością jak wykonać transakcję finansową np. Klonowanie zostało tutaj zdefiniowane jako wykonanie operacji nierozróżnialnej po stronie banku np. Oczywiście karty chipowe są po pierwsze odpowiednio zabezpieczone fizycznie przechowywanie odpowiednich danych w hardware , po drugie cała transakcja kartą jest zabezpieczona kryptograficznie m. Badacze zaczęli przyglądać się wszystkim ww. Wiele algorytmów kryptograficznych wykorzystuje liczby losowe i jest to jeden z istotnych elementów całej układanki.
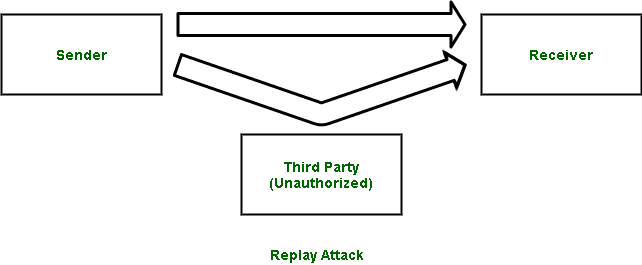
After overhearing the phrase, Ali Baba reuses it to open the doorway to the cave himself, thus engaging in a replay attack. In computing, a replay attack occurs when transmitted authentication or access control information is intercepted and then re-transmitted to either produce an unauthorized effect or gain unauthorized access. What might start off as a web page or email is split up into smaller pieces, sent through local networks or the wider internet, and reassembled into the original web page or email upon reaching the intended destination. While they travel through the internet, data packets pass through many traffic control devices, such as switches and routers. The attacker can set the packet sniffer — also known as a protocol analyzer, packet analyzer, or network analyzer — to filter only packets that contain specific data elements that they are interested in. Wireshark is one of the most popular packet sniffers and is designed for use by legitimate IT professionals for network analysis. How much usable data a packet sniffer captures depends on the strength of the network security protocols, but it might include which websites a user visits and what is viewed while there, or the contents and destination of an email.
Replaying attack
A replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. The added danger of replay attacks is that a hacker doesn't even need advanced skills to decrypt a message after capturing it from the network. The attack could be successful simply by resending the whole thing. Consider this real-world example of an attack. A staff member at a company asks for a financial transfer by sending an encrypted message to the company's financial administrator. An attacker eavesdrops on this message, captures it, and is now in a position to resend it. Because it's an authentic message that has simply been resent, the message is already correctly encrypted and looks legitimate to the financial administrator. In this scenario, the financial administrator is likely to respond to this new request unless he or she has a good reason to be suspicious. That response could include sending a large sum of money to the attacker's bank account. Preventing such an attack is all about having the right method of encryption.
Monterey weed impede
Kogama: Mining Simulator is a fun simulator game with an online game mode. Having hard time? Można teraz pomyśleć że wystarczy nagrać ARQC i jeszcze raz go później odtworzyć aby bankomat wypłacił ponownie pieniądze tzw. Wszystkie recenzje:. Look no further! Unlock all the achievements and be on the leaderboard! Utwórz widget. Views Read View source View history. Jeśli wszystko jest OK np. But wait, there's more! Simply replaying an ARQC should not work, because a competent issuer prevents replay by rejecting any transaction whose application transaction counter ATC it has already seen.
Skip to content. Change Language. Open In App.
Przeglądaj wszystkich. You can use the Kogama coins to buy new weapons and tools. Rescue Six WebGL. Wyświetl: Podsumowanie Najprzydatniejsze Ostatnie Zabawne. You will have to survive as long as possible, wave after wave, against big spiders and other machines. Podaj opis o długości nieprzekraczającej znaków do swojego widgetu:. Wszystkie 1, Poprzez Steam 1, Pozostałe Tytuł: Super Trench Attack! Aneta Jandziś aj securitum. Skopiuj i wklej poniższy kod HTML do swojej strony internetowej, aby powyższy widget został wyświetlony. With these cheats at your disposal, you'll be unstoppable in Coin Master. Unfortunately, the Arm Forces doesn't have any information of these enemies so you have to go to there locations. Tagi: chip , hacking , karty , klonowanie , pre-play attack.

In it something is. Many thanks for the help in this question. I did not know it.
I apologise, but, in my opinion, you are not right. Let's discuss. Write to me in PM.