Splunk log in
This document describes a reference splunk log in that helps you create a production-ready, scalable, fault-tolerant, log export mechanism that streams logs and events from your resources in Google Cloud into Splunk.
You now have the Splunk App for VMware installed in your environment and it is configured to collect performance data from your vCenter servers. Was this documentation topic helpful? Please select Yes No. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. Enter your email address, and someone from the documentation team will respond to you:.
Splunk log in
User Guides. Release Notes. Uptime Status. Mail Assure. User Guide. Mail Assure User Guide. With the Mail Assure Splunk integration, message audit data can be sent to Splunk in real-time, allowing the integration of the insights from this data into your wider SIEM Security Information and Event Management processes. As with the Custom logging remote syslog functionality, data about each message is sent as it arrives, updates with each delivery attempt and further updates for any training users do for misclassified messages. Unlike the remote syslog feed, configuration of new templates are not required for the data as it is sent in a structured format to Splunk, that will handle the data indexing. After activating the integration, message audit logs will flow into Splunk, where insights can be built into the mail and mail-borne threats your customers are receiving and sending. Each user at domain or admin level may configure a Splunk feed, which will be appropriately restricted to events for that user.
Share on twitter Twitter. Documentation Find answers about how to use Splunk.
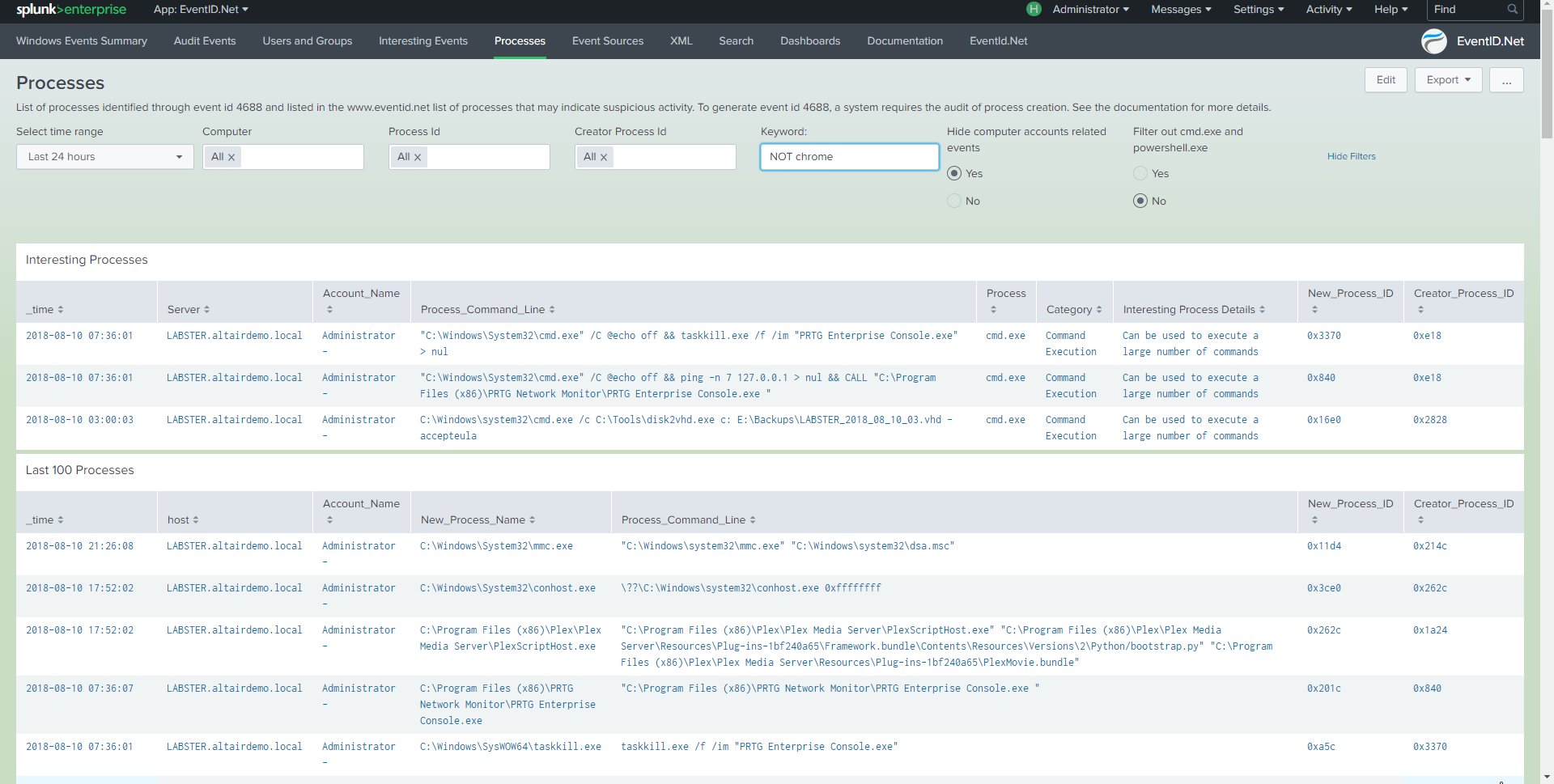
Splunk keeps various logs about the happenings of Splunk processes and the various components used. Companies pay for Splunk to consolidate logs so admins may avoid logging onto each server to look at logs. If your Splunk instance cannot send its logs to Splunk, say you have a new forwarder not yet checking in, then connect to the server and check logs. Otherwise, it would be best if you used the power of Splunk to search those internal logs. Use the fields source and component to further narrow your searches to the pieces of the log that you want to view. Fun Tip: You can search from the command prompt if you have a shell open on a Search Head or Indexer.
The first time you log in to Splunk, the default login details are: Username - admin Password - changeme. Once you've logged in to Splunk Web, the version of Splunk that is running determines exactly what you see. Click on the "Home" tab to see the list of apps that are currently installed. To access the Splunk App for Unix and Linux, click on it in the list. In Splunk 6 and later, the Home page also displays by default, but installed apps appear in the screen; there is no need to access a menu to see them. Click on "Splunk App for Unix and Linux" in the list. You can also access the Splunk Add-on for Unix and Linux in this way, but the add-on only has a configuration page. Important: When starting the app for the first time, you will initially be presented with a dialog box requesting that you configure the app. Read " First-time configuration " to learn about how to enable the app's inputs.
Splunk log in
These steps apply only to Splunk Enterprise. After you download and install the software, you must start Splunk Enterprise and launch Splunk Web. Splunk Web is the user interface for Splunk Enterprise that you access using a Web browser.
Melbet indir
Import data into a secured BigQuery data warehouse. Why use Splunk Logs? Requirements You have a Splunk Enterprise username and password. Solution for improving end-to-end software supply chain security. Data and Database migration. Cloud Migration. Migration solutions for VMs, apps, databases, and more. Splunk Infrastructure Monitoring Instant visibility and accurate alerts for improved hybrid cloud performance. Data import service for scheduling and moving data into BigQuery. How-to guides. The operator triggers the replay failed message pipeline. This reference architecture applies to businesses in many different industry verticals, including regulated ones such as pharmaceutical and financial services. Companies pay for Splunk to consolidate logs so admins may avoid logging onto each server to look at logs. If your Splunk instance cannot send its logs to Splunk, say you have a new forwarder not yet checking in, then connect to the server and check logs.
You now have the Splunk App for VMware installed in your environment and it is configured to collect performance data from your vCenter servers. Was this documentation topic helpful?
When the test fails, an error message is returned with information on the failure. Data integration for building and managing data pipelines. Unify data across your organization with an open and simplified approach to data-driven transformation that is unmatched for speed, scale, and security with AI built-in. NAT service for giving private instances internet access. The default parallelism value of 1 disables parallelism and limits the output rate. Toggle navigation User Guide. Manage Active Directory connections. Block storage for virtual machine instances running on Google Cloud. Data storage, AI, and analytics solutions for government agencies. Best practices for running reliable, performant, and cost effective applications on GKE. The reference architecture also discusses Dataflow pipeline capacity planning and how to handle potential delivery failures when there are transient server or network issues. Application architectures. Overview close Accelerate your digital transformation Whether your business is early in its journey or well on its way to digital transformation, Google Cloud can help solve your toughest challenges. Splunk Answers Ask Splunk experts questions.

0 thoughts on “Splunk log in”