Splunk lookup table
This article briefly discusses at a high level, how to update your Splunk lookup tables with the Tenable app for Splunk. You might just need to refresh it.
Splunk has some enormously powerful features for analyzing data. One of the most popular is the ability to take highly analytical information and render it in ways that are understandable by everyone. This feature is referred to as data enrichment. The function that enables data enrichment is built into Splunk processing language and is called lookups. What are Splunk Lookups? Lookups provide the ability to substitute cryptic information with more readable information without altering the meaning.
Splunk lookup table
Lookups enrich your event data by adding field-value combinations from lookup tables. Splunk software uses lookups to match field-value combinations in your event data with field-value combinations in external lookup tables. If Splunk software finds those field-value combinations in your lookup table, Splunk software will append the corresponding field-value combinations from the table to the events in your search. You can create lookups in Splunk Web through the Settings pages for lookups. If you have Splunk Enterprise or Splunk Light and have access to the configuration files for your Splunk deployment, you can configure lookups by editing configuration files. CSV inline lookup table files and inline lookup definitions that use CSV files are both dataset types. See About datasets. Lookup table files are files that contain a lookup table. A standard lookup pulls fields out of this table and adds them to your events when corresponding fields in the table are matched in your events. All lookup types use lookup tables, but only two lookup types require that you upload a lookup table file: CSV lookups and geospatial lookups. A single lookup table file can be used by multiple lookup definitions.
Choose a general reason -- Choose a general reason Configure custom fields at search time Configure inline extractions Configure advanced extractions with field transforms Configure automatic key-value splunk lookup table extraction Example inline field extraction configurations Example transform field extraction configurations Configure extractions of multivalue fields with fields.
One of the key features of Splunk is Lookups, which allows you to augment your data with information from external sources. Splunk Lookups are a powerful feature that allows you to enrich your data with additional information from external sources. In simple terms, Lookups allow you to add new fields to your data that are not present in the original events. These additional fields can be used to perform more advanced analysis, create reports and dashboards, and gain new insights into your data. Overall, Splunk Lookups are a powerful tool for enhancing your data analysis and gaining new insights into your data. Splunk provides several types of Lookups that you can use to enrich your data with additional information.
I am new to Splunk and trying to figure out how to return a matched term from a CSV table with inputlookup. I just researched and found that inputlookup returns a Boolean response, making it impossible to return the matched term. With that being said, is the any way to search a lookup table and return a matching term? I would imagine eval would do the trick, but I have not been successful in making it work. You can match terms from input lookup on any of the above fields Field1 or Field2 as follows I am matching on Field1 and displaying Field2 :. View solution in original post. Sorry to post comment on an old answer; The solution is working fine but it uses a lot of resources when the number of rows in csv file and index size grow. In my case, I have a structured data file like this:. As there are huge number of events and quite large number of substrings in the csv file, it takes ages to return the result. Great solution!
Splunk lookup table
In this section of the Splunk tutorial you will learn the lookup tables recipes, how to use reverse lookup, using a two-tiered lookup, using multistep lookup, creating a lookup table from search results, and more. These lookup table recipes briefly show the advanced solutions to a common and real-world problem. Splunk lookup feature lets you reference fields in an external CSV file that match fields in your event data. Using this match, you can enrich your event data with additional fields. Note that we do not cover external scripted lookups or time-based lookups.
Schism synonym
Events Join us at an event near you. One lookup table can have multiple lookup definitions. Please reference the saved search to see what sourcetype it uses so that you can view the raw events that contain the available field. Use the configuration files to configure lookups. Interested in learning Splunk? Enroll in our Splunk Training now! The general workflow for creating a CSV lookup in Splunk Web is to upload a file, share the lookup table file, and then create the lookup definition from the lookup table file. You can follow along with the example by performing these steps in Splunk Web. Click Save. Next, we remove duplicates with dedup. In this section of the Splunk tutorial you will learn the lookup tables recipes, how to use reverse lookup, using a two-tiered lookup, using multistep lookup, creating a lookup table from search results, and more. Save this file to a location that is accessible by the Splunk server. Splunk Answers Ask Splunk experts questions.
Lookups enrich your event data by adding field-value combinations from lookup tables.
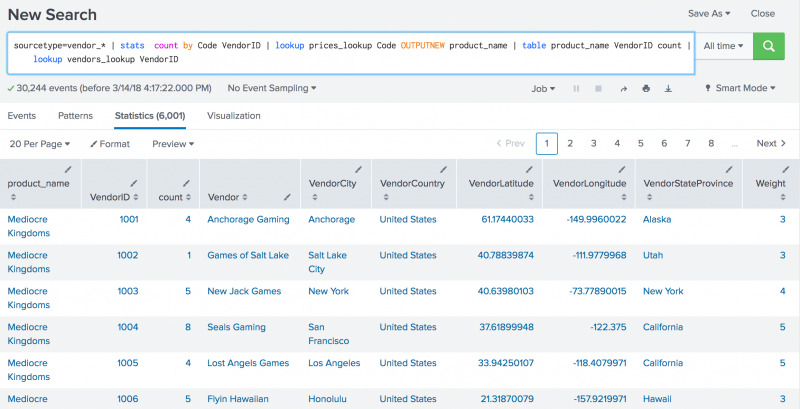
Select a Destination app from the drop-down list. The following search calculates the count of each product sold by each vendor and uses the time range All time. Lookups enrich your event data by adding field-value combinations from lookup tables. How to add a value from a lookup table to results, Internal Commands. User Groups Meet Splunk enthusiasts in your area. How do you use lookups? Application Modernization. You can add the lookup table to your search like this:. Configure custom fields at search time Configure inline extractions Configure advanced extractions with field transforms Configure automatic key-value field extraction Example inline field extraction configurations Example transform field extraction configurations Configure extractions of multivalue fields with fields. Financial Services.

0 thoughts on “Splunk lookup table”