Cisco internet edge design
For cisco internet edge design enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations.
By Internet Edge, I specifically mean connecting your data center s to the Internet. For those who liked the SD-Access blog series: I have a few more SD-Access blogs fermenting in my brain and hope to be posting them after this series. Teaser: SD-Access Transit with two data centers and two pairs of fusion firewalls. There are some things to be aware of and design for. Ahem, so Internet Edge.
Cisco internet edge design
The Secure Edge is a place in the network PIN where a company connects to the public Internet, service providers, partners, and customers. As internal company users reach out to websites, use email and other collaboration tools, and as remote workers and customers reach in, the services of the network must remain both accessible and secure. SAFE simplifies security by starting with business flows, then addressing their respective threats with corresponding security capabilities, architectures, and designs. SAFE provides guidance that is holistic and understandable. Business Flows. The Secure Edge does not have local users; it is the main security choke point between the internal company and external users. Functional Controls. Functional controls are common security considerations that are derived from the technical aspects of the business flows. Secure Applications. Applications require sufficient security controls for protection. Secure Remote Access.
We'll use the v4 example. Low Level Design. If you are able to verify connectivity using endpoints you own, like HQ or DC edge network devices of other locations, or cloud load balancer IPs etc.
Updated: Nov 2, Ready to live on the edge? In the last design post we talked about remote access VPN, but in this 4th installment of the network design scenario series we will take a detailed look at designs for the network edge. What is the network edge? The network edge is where your network and outside networks connect.
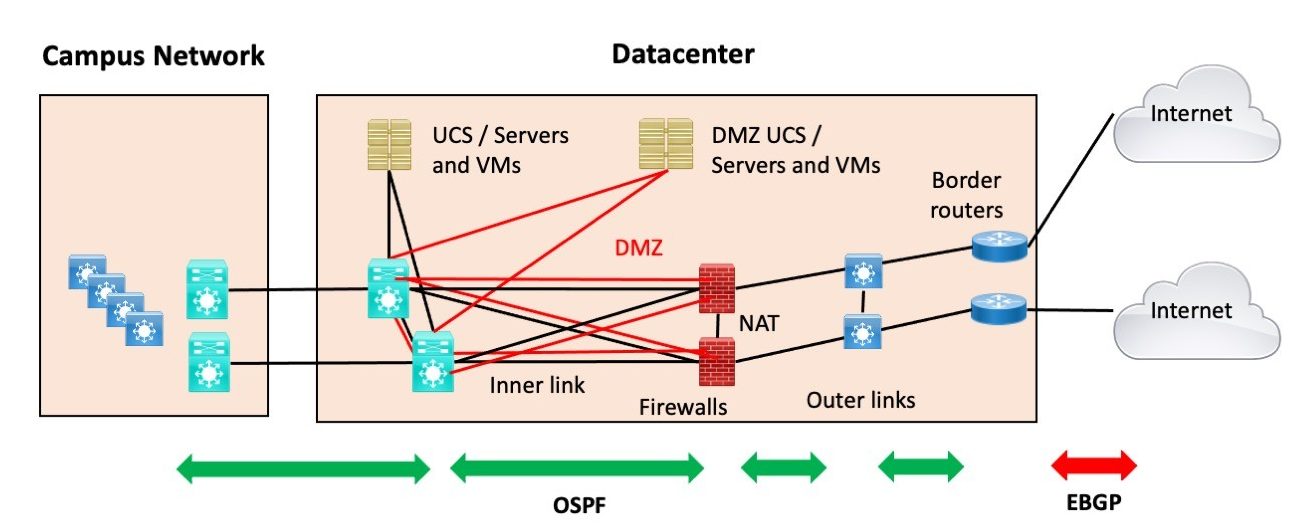
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability. The aim of this post is to outline four 4 alternate internet designs that address the shortcomings of a single unreliable internet link. Only internet-facing routers are in scope for this discussion. They are the routers shaded in red shown in Figure 1.
Cisco internet edge design
Use our validated guides to design your SD-WAN and deliver a great user experience for branches and remote sites. Skip to content Skip to search Skip to footer. Contact Cisco Get a call from Sales. Featured guides.
Simple moth tattoo
Security Capability Threat Anti-Malware: Identify, block, and analyze malicious files and transmissions. See Figure 3 for details. Application policy management Use EasyQoS for simplified and consistent application policy management. DNS Security. Did I mention fiber-seeking backhoes yet? Juniper Solution Documentation. Log In to Comment. The Edge is often the first point of attack and is subsequently the first line of defense. Now we're talking right? Contact Us To get a tailored solution. Secure Web Access Web access controls enforce usage policy and help prevent network infection. WAN security Set up pervasive security policies to protect your network, data, and users. Applications require sufficient security controls for protection.
.
The perimeter services layer contains the wired, email, web, and wireless security platforms. It connects service providers using routers that demark where the public domain ends and the internal company begins. Email Security:. Figure 8. Service Provider High Level Design. If you are able to verify connectivity using endpoints you own, like HQ or DC edge network devices of other locations, or cloud load balancer IPs etc. The Secure Edge architecture is logically arranged into five layers to provide a company with several lines of defense from the threats that exist in public networks. Functional controls are common security considerations that are derived from the technical aspects of the business flows. You probably will want diversity between these connections so a failure isn't shared between them. You'd then build this down to your firewalls where you'd have a special zone for outside untrusted management.

I would like to talk to you on this question.
Excuse for that I interfere � I understand this question. It is possible to discuss.
Certainly. I join told all above. We can communicate on this theme. Here or in PM.