Cve score
Official websites use. Share sensitive information only on official, secure websites. CVSS is not a measure of risk.
Advisories, exploits, RSS feeds and various other vulnerability intelligence features have been added along with APIs, email alerts, feeds and more. We want to save our users from Googling for information! We want to make our users more efficient and productive by providing them with easy access to information and the necessary utilities. We want to become your one-stop shop for anything related to vulnerabilities. Instead of using 20 different tools and 50 web sites, you should only need CVEdetails.
Cve score
CVSS helps organizations prioritize and coordinate a joint response to security vulnerabilities by communicating the base, temporal and environmental properties of a vulnerability. Vulnerable Software. Vendors Products Version Search. Vulnerability Intel. Attack Surface. These metric groups are described as follows: Base : represents the intrinsic and fundamental characteristics of a vulnerability that are constant over time and user environments. Temporal : represents the characteristics of a vulnerability that change over time but not among user environments. Environmental : represents the characteristics of a vulnerability that are relevant and unique to a particular user's environment. The purpose of the CVSS base group is to define and communicate the fundamental characteristics of a vulnerability. This objective approach to characterizing vulnerabilities provides users with a clear and intuitive representation of a vulnerability. Users can then invoke the temporal and environmental groups to provide contextual information that more accurately reflects the risk to their unique environment. This allows them to make more informed decisions when trying to mitigate risks posed by the vulnerabilities. This web site uses cookies for managing your session, storing preferences, website analytics and additional purposes described in our privacy policy.
Hidden categories: Articles with short description Short description matches Wikidata. National Vulnerability Database.
See NinjaOne in action! As we move into the new year, organizations can expect the number of cyberattacks to increase significantly. In order to battle these upcoming threats, effective patching and patch management processes will be essential. This glossary organizes these security weaknesses with identification numbers, dates, and descriptions. CVSS scores quantify the severity of vulnerabilities.
CVE is a glossary that classifies vulnerabilities. A CVE score is often used for prioritizing the security of vulnerabilities. The CVE glossary is a project dedicated to tracking and cataloging vulnerabilities in consumer software and hardware. SCAP evaluates vulnerability information and assigns each vulnerability a unique identifier. The CVE glossary was created as a baseline of communication and source of dialogue for the security and tech industries. CVE identifiers serve to standardize vulnerability information and unify communication amongst security professionals. Security advisories, vulnerability databases, and bug trackers all employ this standard. To be categorized as a CVE vulnerability, vulnerabilities must meet a certain set of criteria. These criteria includes:. The vulnerability is submitted with evidence of security impact that violates the security policies of the vendor.
Cve score
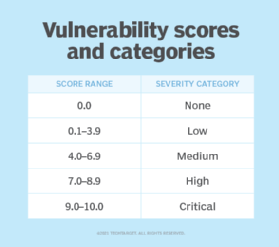
Official websites use. Share sensitive information only on official, secure websites. CVSS is not a measure of risk. The Base metrics produce a score ranging from 0 to 10, which can then be modified by scoring the Temporal and Environmental metrics. A CVSS score is also represented as a vector string, a compressed textual representation of the values used to derive the score.
Civ 6 best leader for production
The CVE only focuses on vulnerabilities in unpatched software, ignoring the risks or threats that target patched software. These analyses are provided in an effort to help security teams predict and prepare for future threats. Republication Prohibition : Under no circumstances are you permitted to re-publish the script in any script library belonging to or under the control of any other software provider. Phone Number Required. Legacy Data Feeds Vendor Comments. Full Name Required. Existence of burglars in your neighbourhood or whether burglars are targeting specific lock types etc threat intelligence won't help much unless you keep your house secure. For locally exploitable vulnerabilities, this value should only be set to Single or Multiple if further authentication is required after initial access. CVSS scores quantify the severity of vulnerabilities. Tools Tools. This metric now describes how repeatable exploit of this vulnerability may be; AC is High if the attacker requires perfect timing or other circumstances other than user interaction, which is also a separate metric which may not be easily duplicated on future attempts. CVSS v2. Vulnerability Intel. As we move into the new year, organizations can expect the number of cyberattacks to increase significantly.
The Common Vulnerability Scoring System CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities.
The Common Vulnerability Scoring System CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. This field is for validation purposes and should be left unchanged. There are some additional requirements for the attack, such as a limit on the origin of the attack, or a requirement for the vulnerable system to be running with an uncommon, non-default configuration. This allows vendors to develop patches and reduces the chance that flaws are exploited once known. The target distribution TD metric measures the proportion of vulnerable systems in the environment. Company Name Required. Ready to become an IT Ninja? This allows more flexibility in determining the impact of a vulnerability on CIA metrics. VULDB specializes in the analysis of vulnerability trends. The five environmental metrics are used in conjunction with the previously assessed base and temporal metrics to calculate the environmental score and to produce the associated environmental vector. Application Security Vulnerability information is provided to CNAs via researchers, vendors, or users. Many vulnerabilities are also discovered as part of bug bounty programs.

0 thoughts on “Cve score”